“Consensus” in cryptocurrency refers to an automated mechanism for a network to agree on a single, valid state of the blockchain. Consensus is critical in distributed networks, because it ensures that any given transaction on the blockchain is authentic, verified, and agreed upon amongst distributed nodes. It also removes the necessity for any one centralized (or human) entity to verify transactions. Consensus ensures security, accuracy, and authenticity of digital transactions, and ultimately maintains the integrity of the network.
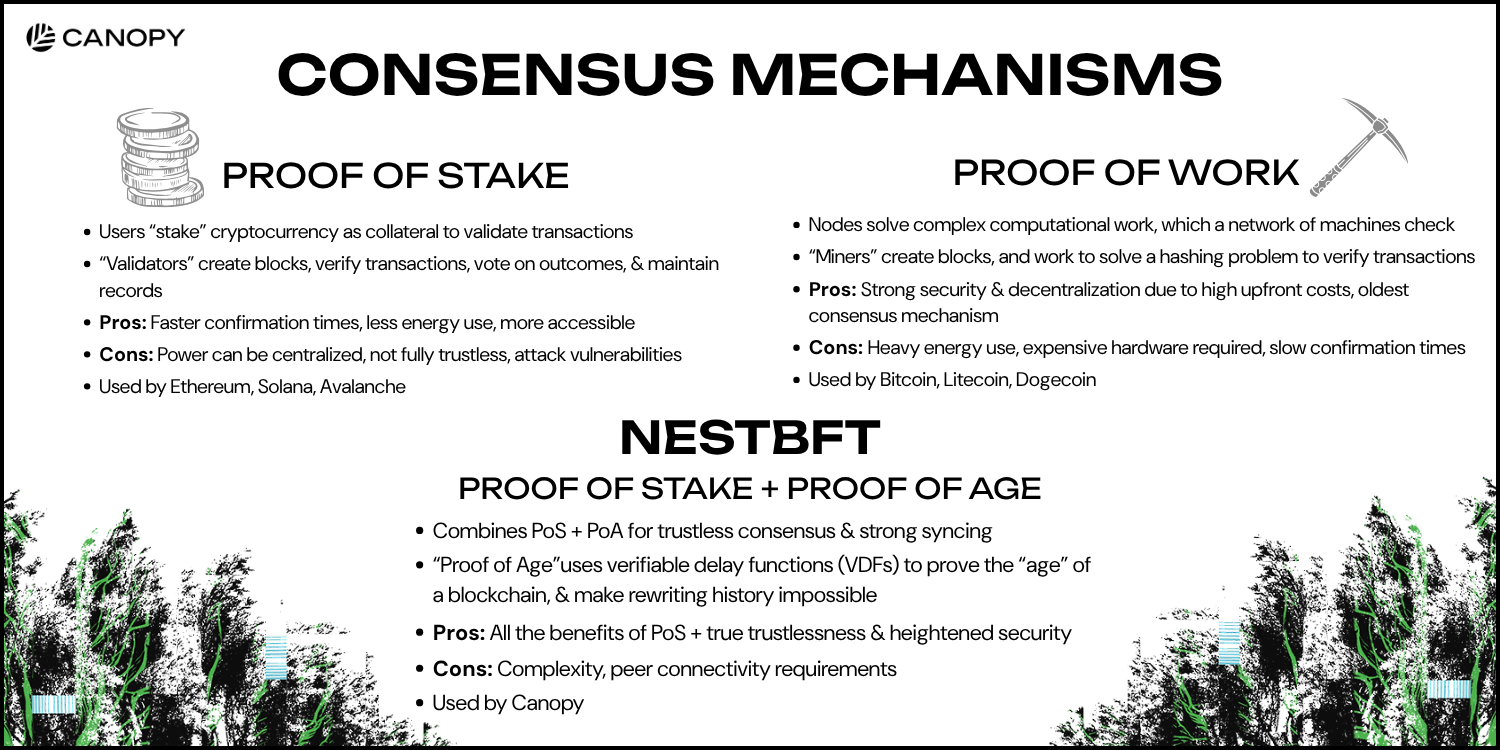
Proof of Work (PoW) is a widely used consensus method behind major cryptocurrencies like Bitcoin and Litecoin. In PoW, a node must demonstrate that it performed valid computational work, which a broad network of machines then checks. This approach, particularly in Bitcoin, is known for heavy energy use (and resulting environmental impact), along with relatively slow confirmation times.
Proof of Stake emerged as a lower-cost, lower-energy alternative to PoW. In PoS systems, such as Ethereum Proof of Stake, the right to propose a new block is assigned to participants in proportion to how many tokens they hold. The rest of the network validates the proposal and, if agreement is reached, the block is appended to the blockchain.
While many see Proof of Stake as a natural evolution to Proof of Work, it also comes with its fair share of drawbacks. Let’s dig in, and explore how emerging consensus mechanisms can address these issues.
One of the major criticisms of Proof of Stake is in its inherent need for “trust,” which contradicts the benefits of decentralization. Every major Proof of Stake blockchain today, from Ethereum to Polkadot, shares a dirty secret: they can't trustlessly sync their own blockchain.
This isn't a bug. It's a fundamental limitation of PoS consensus that forces networks to rely on centralized checkpointing, social consensus, and "weak subjectivity" to prevent catastrophic attacks. Ethereum co-founder, Vitalik Buterin, acknowledged this trade-off when he wrote about learning to "love weak subjectivity" in 2014.
The consequences? Reduced decentralization, vulnerability to long-range attacks, and blockchain finality that ultimately depends on trust rather than cryptography.
What if we could solve this?
NestBFT is Canopy Network's novel consensus mechanism designed to address the core limitations of existing Byzantine Fault Tolerant (BFT) systems, such as PoW and PoS. Built from the ground up for Canopy, NestBFT combines proven cryptographic techniques with innovative architectural choices to deliver:
Unlike legacy BFT implementations that assume reliable network conditions, NestBFT is engineered for real-world peer-to-peer environments where delays and interruptions are inevitable.
So, what does NestBFT allow for in the blockchain space?
NestBFT isn't just a technical improvement — it's an architectural enabler for Canopy's blockchain model. NestBFT offers a robust set of advantages for various stakeholders.
For L1-based applications, it delivers immediate economic security through shared validators, and provides production-grade consensus without the usual development complexities. It ensures preserved finality, even after an L1-based application achieves independence, and includes built-in protection against bootstrapping vulnerabilities.
For the wider ecosystem, NestBFT fosters true decentralization, by eliminating the need for centralized checkpointing. It promotes capital-efficient security through restaking and demonstrates resilience against both long-range and DDoS attacks. Ultimately, it achieves optimal performance even in demanding real-world network conditions.
For the advancement of blockchain innovation, NestBFT serves as a powerful evolution. It proves that Proof of Stake can indeed be trustless with the right cryptographic primitives, that consensus can be both simple and sophisticated, and that robust security doesn't necessitate sacrificing decentralization.
So, how does NestBFT work, and what enables it to be truly novel?
The breakthrough that enables trustless PoS is NestBFT's use of Verifiable Delay Functions (VDFs) as a reliable proxy for elapsed time.
Verifiable-Delay-Functions are cryptographic constructs — essentially, mathematical problems — that require the execution of a series of sequential calculations to solve, and are resistant to hardware speedups. Once solved, they can be verified quickly and efficiently.
In long-range attacks, adversaries acquire old validator keys cheaply and rewrite blockchain history from deep in the past. Because PoS has no external "proof of work," there's no way to verify which chain is the "real" one without relying on social consensus.
VDFs can solve this problem. With NestBFT, every block includes a VDF, proving sequential computation over the expected approximate block time. This creates temporal consistency that makes rewriting history computationally infeasible — attackers would need both the keys AND real elapsed time to create a competing chain.
Key advantages:
This represents a fundamental shift: from Proof of Stake (which requires trust) to what we call Proof of Age (which is cryptographically verifiable).
Traditional BFT systems face two critical attack vectors. First, they are vulnerable to DDoS attacks. Tendermint's predictable round-robin leader selection makes future leaders easy to identify and overwhelm, even with "sentry node" protections. Second, grinding attacks are possible. Introducing randomness to prevent DDoS often creates opportunities for leaders to manipulate selection by altering block contents or parameters.
NestBFT's VRF-based election solves both:
The seed data consists of Last_Proposer_Addresses + Height + Round, ensuring unique input for each consensus view that cannot be manipulated by any single leader. Each validator then computes their VRF output:
VRFOut = Hash(BLS_Private_Key.Sign(Seed))
The seed is non-manipulable (based on past consensus results) and unpredictable (unique per round). Each validator privately computes their VRF output and threshold to determine if they're a candidate:
CandidateCutoff = (voting_power × expected_candidates) / totalVotingPower
IsCandidate = toNumberBetween0And1(VRFOut) < CandidateCutoff
Multiple candidates are expected — the one with the smallest VRFOut wins. If no candidates emerge, the system falls back to stake-weighted pseudorandom selection (still grinding-immune but less DDoS-resistant).
The elegant design of the system offers several key advantages. It effectively hides leaders until they formally announce their candidacy, providing crucial protection against distributed denial-of-service (DDoS) attacks. Furthermore, it incorporates non-grindable seeds, a vital feature that safeguards against manipulation. The system also ensures that fairness is maintained through a stake-weighted mechanism, and notably, it requires no complex coordination among participants.
Network asynchrony is inevitable in distributed systems. When validators fall out of sync, how quickly can they recover? Legacy implementations like Tendermint use fixed timeouts that either waste time (if too long) or fail to account for actual network conditions (if too short). NestBFT's pacemaker uses a communication phase where validators gossip their current round, then calculates the highest round witnessed by a supermajority of stake. The system jumps directly to that round.
Phase wait times increase linearly with each round:
phase_wait = round × initial_phase_Δ
This adaptive approach ensures rapid resynchronization without unnecessary delays, optimizing for both network speed and fault tolerance.
NestBFT achieves consensus through eight core phases, each designed for specific verification and aggregation tasks:
Two recovery phases (Round_Interrupt and Pacemaker) handle network disruptions.
Each phase uses BLS signature aggregation for O(1) space complexity while maintaining a star communication pattern for linear communication complexity, making NestBFT highly efficient even at scale. Blocks receive immediate finality with no need for additional confirmation, a critical feature for L1-based applications that may eventually graduate to independence.
For developers interested in implementation details:
Full specification available in our whitepaper and documentation.
NestBFT represents more than an incremental improvement to existing consensus mechanisms, it's a fundamental rethinking of how blockchain security, decentralization, and scalability can coexist.
By solving the trusted synchronization problem inherent in Proof of Stake, eliminating single points of failure in leader election, and providing verifiable temporal consistency through VDFs, NestBFT enables a new category of blockchain infrastructure: progressive autonomy.
Applications can start small, scale with confidence, and graduate to independence without compromising security or rewriting core infrastructure. This is consensus designed for evolution, not lock-in.